In today’s digital world, organizations face a growing number of cyber threats. These can compromise sensitive data, disrupt daily operations, and damage your reputation. Businesses are vulnerable to these risks without proper cyber security risk assessment. Read on for a step-by-step guide to perform a cyber security risk assessment so you can stay ahead of threats.
5 Steps to Perform a Cyber Security Risk Assessment
Determine the scope of the risk assessment
Start by determining the scope of your cyber security risk assessment. This means identifying which systems, networks, and data you will assess. This clarity is important because it ensures your security team focuses on the most essential assets and vulnerabilities. A clear scope means you can allocate resources effectively and ensure a thorough evaluation.
Identify assets and threats
Next, identify your organization’s valuable assets, as well as potential threats. Assets can include:
- hardware
- operations systems
- programs
- data
Use frameworks like NIST to guide your process. After you identify assets, you should also identify threats. This can include:
- cyberattacks
- natural disasters
- human error
- supply chain issues
This process is essential to understanding what needs protection and what kinds of threats your organization faces.
Determine the potential impact of threats
After the identification process, assess how these threats could impact your organization. Evaluate how an attack could affect your:
- daily operations
- finances
- reputation
- compliance status
Consider the likelihood and severity of each threat to understand your overall risk level.
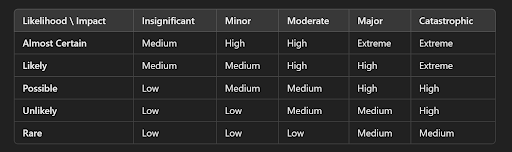
Prioritize your risks
After the analysis phase, prioritize the risks based on their likelihood and impact. This will help you focus your efforts on the most significant threats first. Develop a risk matrix to rank these risks. This helps your security team implement controls where you need them most.
Document risks
Finally, document all identified and prioritized risks. This documentation should include details about:
- assets
- threats
- potential impacts
- the prioritization process
Maintaining a detailed record provides a reference point for future assessments. It also helps to monitor the effectiveness of security measures and ensures regulatory compliance.
Constructure Technologies is a leading provider of voice and data solutions. Follow our blog and connect with us on social media to learn more cyber security tips.
Instagram
Facebook
LinkedIn
Twitter

